Optimal targeted advertising strategy for secure wireless edge metaverse
Published in In IEEE Global Communications Conference (GLOBECOM), 2022
Recommended citation: Hongyang Du, Dusit Niyato, Jiawen Kang, Dong In Kim, and Chunyan Miao. "Optimal Targeted Advertising Strategy For Secure Wireless Edge Metaverse." In IEEE Global Communications Conference (GLOBECOM), 2022. https://arxiv.org/abs/2111.00511
Abstract: Recently, Metaverse has attracted increasing attention from both industry and academia, because of the significant potential to integrate real and digital worlds ever more seamlessly. By combining advanced wireless communications, edge computing and virtual reality (VR) technologies into Metaverse, a multidimensional, intelligent and powerful wireless edge Metaverse is created for future human society. In this paper, we design a privacy preserving targeted advertising strategy for the wireless edge Metaverse. Specifically, a Metaverse service provider (MSP) allocates bandwidth to the VR users so that the users can access Metaverse from edge access points. To protect users’ privacy, the covert communication technique is used in the downlink. Then, the MSP can offer high-quality access services to earn more profits. Motivated by the concept of “covert”, targeted advertising is used to promote the sale of bandwidth and ensure that the advertising strategy cannot be detected by competitors who may make counter-offer and by attackers who want to disrupt the services. We derive the best advertising strategy in terms of budget input, with the help of the Vidale-Wolfe model and Hamiltonian function. Furthermore, we propose a novel metric named Meta-Immersion to represent the user’s experience feelings. The performance evaluation shows that the MSP can boost its revenue with an optimal targeted advertising strategy, especially compared with that without the advertising.
Index Terms: Metaverse, targeted advertising, covert communication, bandwidth allocation
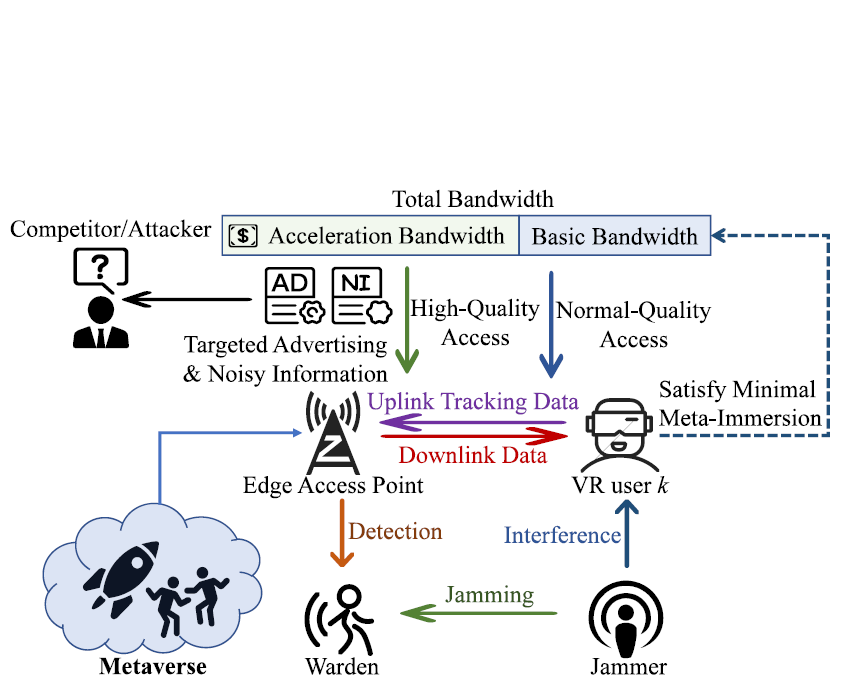
Fig. 1: System model of Metaverse covert access and target advertising.
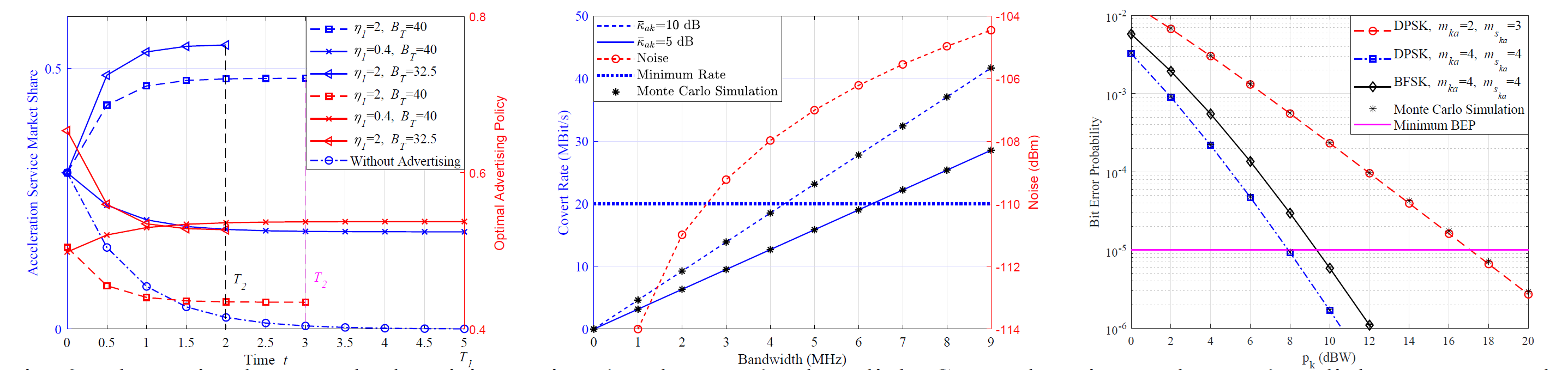
Fig. 3-5: Simulation results are presented to verify the proposed analysis.
